Pertuniti supports two-factor authentication via WebAuthn. This allows to set up security keys (e.g. YubiKey, Swissbit iShield, Google Titan and many more) as well as smartphones (passkeys) as a second factor.
Table of contents
- Why WebAuthn?
- Setting up a security key or passkey
- Login via security key or passkey
- I have lost my security key or smartphone
Appendix A. Compatibility of security keys
1. Why WebAuthn?
Sadly, loggin in only via username (e-mail address) and password can no longer be considered secure, since passwords are often reusted for several platforms — and once email-password-combinations are leaked, the are quickly tried out on other websites as well. Even if secure passwords are carefully chosen and used only once, well-crafted phishing websites can be effective and provide login credentials to unauthorized persons.
Therefore, Pertuniti generally relies on two-factor authentication. By default, it asks you for a one-time password, which you receive via email. A leaked password alone is therefore not sufficient to access Pertuniti. However, this approach does not protect against phishing, which is why we also support the standard WebAuthn for login.
In general, we recommend using security keys or passkeys via smartphones as a second factor, since authentication via WebAuthn also takes the domain name into account and is therefore usually referred to as “phishing-resistant”. This article explains how to set up a security key or passkey.
2. Setting up a security key or passkey
Regardless of whether you want to set up a physical security key or passkey via smartphone, you will start the same way:
- Open the settings (menu on the top right of your abbreviation or profile picture).
- Open “Security keys” in the menu group “Security”
You can open these settings directly: https://app.pertuniti.com/#/config/security-keys
Without a security key set up, the following view is displayed:
Now go to “Register new key”. Give the key or passkey a meaningful name with which you can easily identify it yourself, e.g. “Johanness’ Yubikey” or “iPhone 15”. If you lose your device, you can easily remove the entry this way. An entry can look like this, for example:
By clicking on “Register” you have two options:
2.1 Setting up a physical security key
Pertuniti supports numerous security keys that adhere to the WebAuthn or FIDO2 standard. In Appendix A, we list compatible security keys, but many more will work as well.
2.2 Setting up a passkey via your smartphone
You can also set up your smartphone as a second factor. Give it a speaking name as well, click on register and you can see the following QR code:
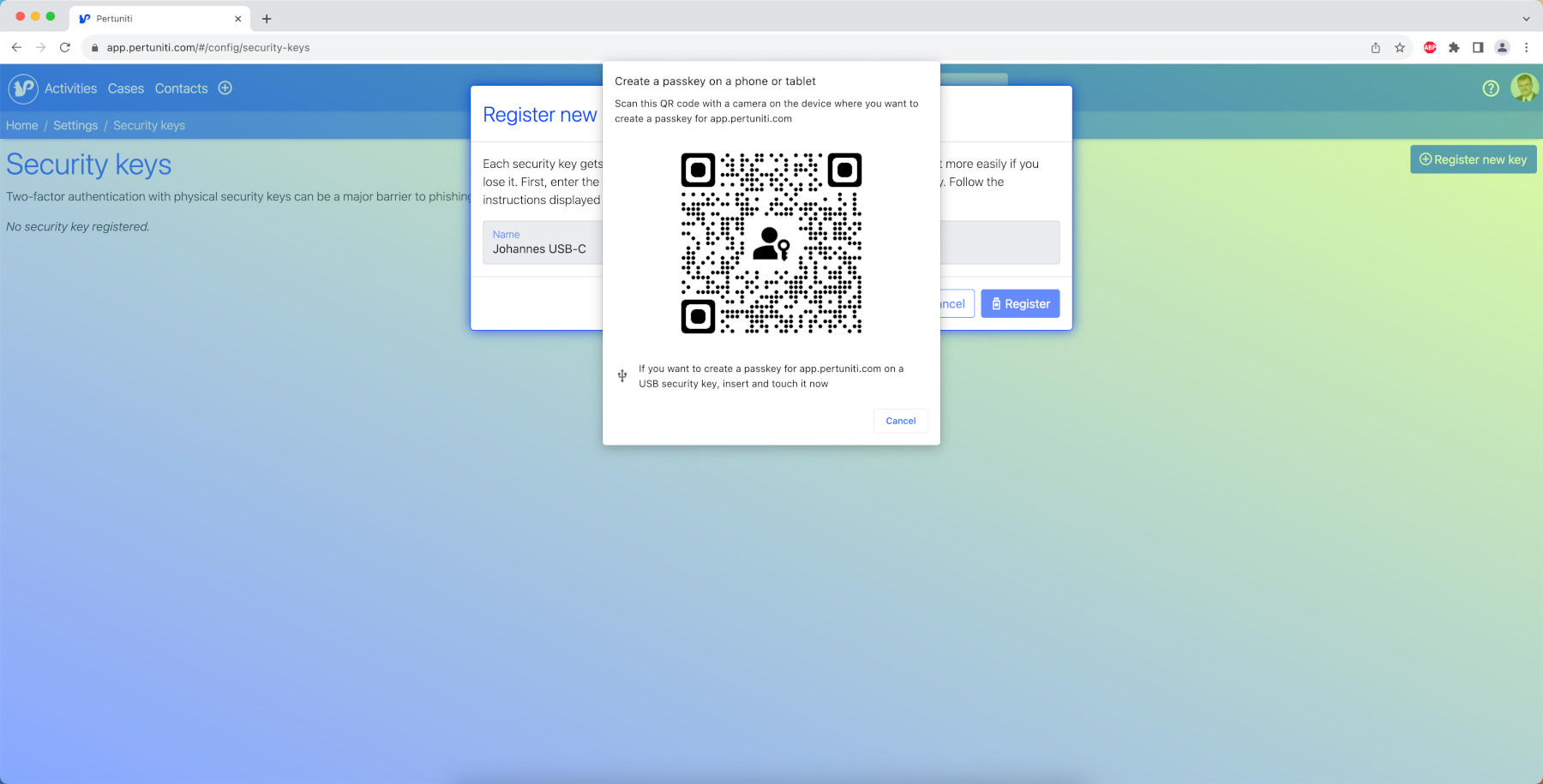
Scan the QR code on your mobile device and follow the steps displayed on it.
2.3 Configured security key or passkey
After you have set up a security key or passkey, it will be displayed in the list of security keys, for example:
In this view, you can remove lost security keys or smartphones so that they are no longer treated as a second factor for logging in.
3. Login via security key or passkey
You can now log in with the newly set up security key or passkey. If you want to test this, first log out (Menu > Logout) and enter your username and password. You will then be asked for your new second factor:
4. I have lost my security key or smartphone
Pertuniti expects a second factor for the login, which of course does not work if this physical second factor is lost.
By default, Pertuniti still supports login via email code in case of a failed login via security key. Therefore, if in doubt, use this option.
For Enterprise customers only: If you have disabled login via e-mail for your organization, we recommend registering a second security key that is kept in a safe place and can be used to login if the other security key is lost. Otherwise, your next successful login will depend on the customer-specific conditions for recovering a lost key.
After a successful login, you should remove the lost key from the list of security keys.
Appendix A. Compatibility of security keys
| Name | Manufacturer | Interface | Made in | Compatibility | ||||
|---|---|---|---|---|---|---|---|---|
| Windows (11) | macOS (Ventura) | Ubuntu (23.04) | iOS (16) | Android (13) | ||||
| Google Titan Security Key | USB-C, NFC | USA & China | 1) | |||||
| Swissbit iShield Key Pro | Swissbit | USB-A, NFC | Germany | 2) | ||||
| Swissbit iShield Key FIDO2 | Swissbit | USB-A, NFC | Germany | 2) | ||||
| YubiKey Security Key NFC | Yubico | USB-A, NFC | Sweden & USA | |||||
| YubiKey Security Key C NFC | Yubico | USB-C, NFC | Sweden & USA | |||||
- Windows (11): Chrome, Edge, Firefox
- macOS (Ventura): Safari, Chrome
- Ubuntu (23.04): Firefox, Chromium
- iOS (16): Safari (connected via NFC)
- Android (13): Chrome (connected via USB-C and adapter for USB-A)



